CSF, A Powerful and Easy to Control Firewall for Linux Servers
ConfigServer Security & Firewall, commonly known as CSF, is one of the most popular firewall...
“IMAP Auth process broken 993” Error
The error “IMAP Auth process broken 993” generally means that the authentication (auth) daemon for...
In-Depth Comparison Between ImunifyAV and ClamAV, Expert and Community Assessment
ImunifyAV and ClamAV were created to solve the same fundamental problem: detecting malware on servers....
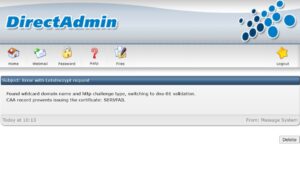
Detailed Explanation of the CAA Error, Its Causes, and How to Configure CAA Correctly for Successful SSL Issuance
During the process of issuing an SSL certificate, especially when using Let’s Encrypt or automated...
Cloud Server and VPS: Where the Real Differences Lie? A Comprehensive Analysis
In the world of digital infrastructure, two concepts that seem familiar to everyone—Cloud Server and...
ConfigServer Security & Firewall (CSF): Introduction, Installation, and Security Best Practices
ConfigServer Security & Firewall (CSF) is a free, advanced firewall for Linux, and also an...
Introduction to ModSecurity, its advantages and disadvantages.
1. What is ModSecurity? ModSecurity is an open-source Web Application Firewall (WAF) that acts as...
Detailed comparison between Redis Cache and Memcached Cache
1. Quick Overview Criterion Redis Memcached Type In‑memory datastore with rich data types Simple in‑memory...
Full Introduction to W3 Total Cache
🔷 What is W3 Total Cache? W3 Total Cache (W3TC) is a WordPress caching plugin...
Introduction to WP Super Cache
WP Super Cache is a free WordPress caching plugin developed by Automattic – the company...